Cyber Security
Cyber Security
Definition: In today’s time, it is widely used. It is a type of security that is related to the Internet. It involves protecting hardware, software, and data from cybercrimes.
These days, cyber security is often at risk because network connections and the internet are being used rapidly, which has the power to change the world. Nowadays, everything has become more digital, making security extremely important.
The administration is adopting various methods to solve this kind of problem. Help is being sought from many countries for cybersecurity, ensuring that the nation’s private data does not leak and all information remains secure.
NOTE: In 2017, Gartner Company estimated that global spending on information security had increased to 83.4 billion, which is approximately a 7% increase from 2016. It is projected that by the end of 2018, spending on its products and services will reach 93 billion.Types of Cybersecurity Attacks
Ransomware –
This is a type of virus that criminals use to infect others’ computers or systems. It corrupts the files stored on the computer.
Malware –
It refers to files or programs that cause damage to the computer, such as computer viruses, worms, etc.
Social engineering
It is a type of attack that relies on humans, aimed at cleverly tricking people to extract their personal data, passwords, etc.
Phishing –
It is a type of fraud in which fraudsters send emails to deceive people and steal data. The email appears to be from a legitimate organization. In this way, data is stolen, such as credit card information or login credentials.
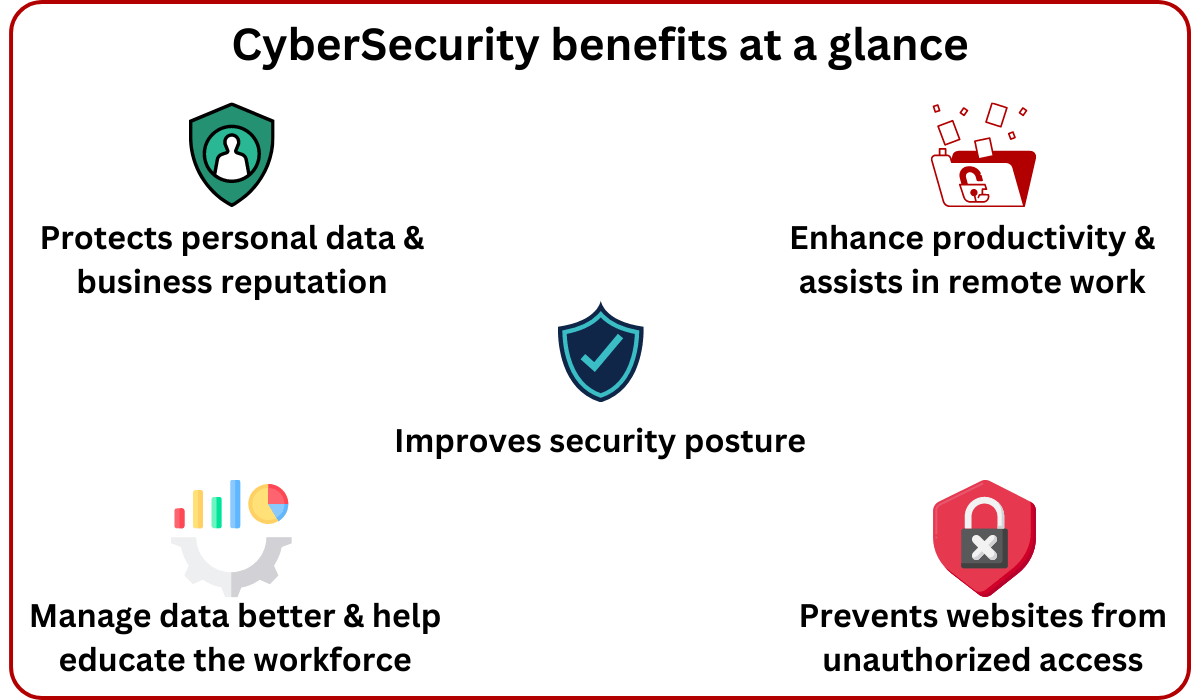
The Benefits of Cyber Security
Cyber security is essential because governments, military, corporate, financial, and medical institutions collect various types of data and store that data in their systems, computers, and other devices. Some of this data can be very important, and its theft can have a profound impact on an individual’s private life, potentially ruining the reputation of the institution involved.
With the help of cyber security, this vast amount of data is kept safe so that it does not fall into the wrong hands. As the amount of data increases, we require better and more effective cyber security products and services.
Cyber security helps us protect against cyberattacks, data theft, and threats from criminals. Whenever an organization has robust network security and methods to avoid any kind of difficulty, it is all made possible through cyber security products and services. For example, various types of antivirus software protect us from virus attacks.
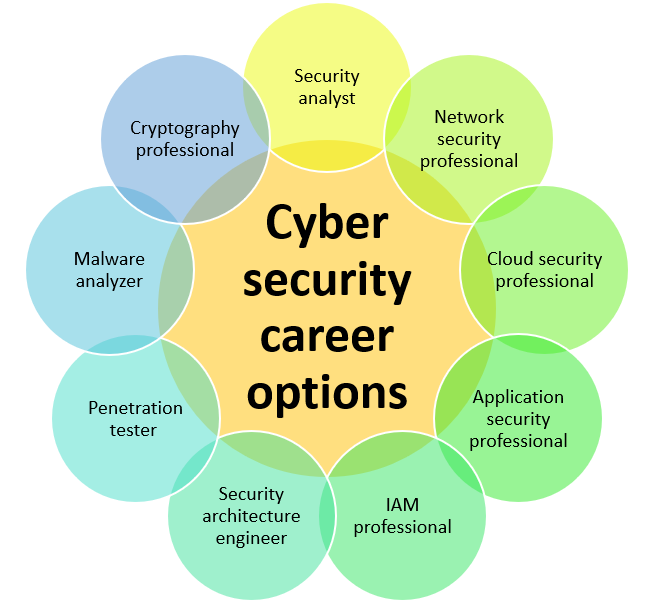
Careers in Cyber Security
As the pace of cyber threats continues to increase, the need for hardware and software to protect against these attacks is also growing. Additionally, those who are responsible for security are facing challenges as well. Those who work to protect cyber security are at risk today.
It is being reported that there are at least 1 million job openings in cyber security worldwide. IT professionals and computer experts are equipped for these types of cyber security jobs. To protect against these threats, it is essential to consider these opportunities
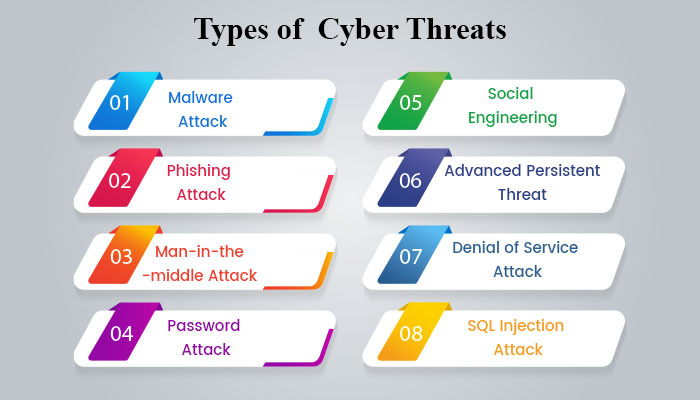
Threats to Security
This is a type of problem that exploits a vulnerability to gain access to a computer, thereby compromising security and potentially causing significant harm. This can lead to data loss and may damage our hardware.
A security threat is a type of risk that can harm a computer system or organization. This can involve the theft of our system’s data or a virus attack that damages our computer system. All data can be leaked and misused.
Security threats are mainly of two types:
- Non-Physical threats
- Physical threats
Non-Physical Threats
Non-physical threats are also known as logical threats. In this, the attack is carried out through viruses, worms, Trojan horses, etc.
The following is a list of common types of non-physical threats:
- Virus
- Trojans
- Worms
- Spyware
- Keyloggers
- Adware
- Denial of Service Attacks
- Distributed Denial of Service Attacks (DDoS)
- Phishing
- Other computer threats
Physical Threats
Physical threats are of three types:
Internal: This includes fire outbreaks, unstable power supply, room humidity (moisture), etc.
External: This includes lightning strikes, floods, earthquakes, etc.
Human: This includes theft by a person, damage to hardware, or accidentally breaking the system, etc.
CSA:
Computer Network Architecture describes how computers are arranged and how their functions are allocated to them. Computer network architecture determines the physical and logical design of software, hardware, protocols, and transmission media, and how they communicate with each other.
When we arrange multiple computers together.
Types of Computer Network Architecture :
· Peer to Peer Network Architecture
· Client-Server Network Architecture
· Hybrid Network Architecture
Peer to Peer Network Architecture –
Peer to Peer networks are also referred to as point-to-point networks. They are easy to set up because it is a type of network in which all computers are connected to each other.
Client-Server Network Architecture –
The client-server network architecture consists of a central controller known as the server, which controls all the devices in the network. All other devices are referred to as clients.
Hybrid Network Architecture –
The hybrid network architecture is composed of both peer-to-peer and client-server network architectures. It contains features of both types of networks.


Comments
Post a Comment